Risk-Based Approach for – CSV – Beyond GXP
October 31, 2022 Vitaly ShlimovichRisk-Based Approach for – CSV – Beyond GXP
October 31, 2022
Vitaly Shlimovich
Do you work with software that manages important or even crucial processes in your organization? Are you sure that the results these programs deliver are correct and consistent?
Validation of computerized systems is required for all GXP processes. It is also a useful tool for other fields to make sure the software works well and your information is safe.
In this article, you will find answers to
1- What is the conventional risk-based approach to computerized system validation?
2- What additional risks and regulations can be addressed?
What is the conventional risk-based approach to computerized system validation?
The GAMP5 is currently the most widely used industry guidance. It advises businesses to concentrate on critical aspects of their computerized systems and use them to develop controls to reduce the risk of system failure. This is where a thorough understanding of the product and process is critical in determining the potential risks to individual safety.
Essentially, the guidance focuses on understanding the system and the process in which it is involved, allowing us to identify the critical functions that impact patient safety, product quality, and data integrity. They are commonly referred to as GxP-relevant functions. Following the implementation and verification of relevant appropriate controls to address the risks, we either redesign the system to eliminate the issues or verify the functionality to demonstrate that the risks can be managed at an acceptable level through execution IQ, OQ, and PQ testing.
What additional risks and regulations can be addressed?
A computerized system frequently plays such a critical business role that we would like it to be verified not only within GxP-relevant processes but also within other realms of critical business processes.
Specific functionality may, for example, generate a financial report to be submitted to public agencies, provide data to a Financial Consolidation System, or support other financial activities that are not necessarily regulated by the relevant regulation (SOX).
Alternatively, specific functionality is used to create, manage, or host personal information about individuals (GDPR), or to manage legal or contract data or transactions.
A system function can be critical for the business in general, like impacting the operations in a way that may lead to stopping the production, shipping, or invoicing process or even lead to legal issues.
How to approach it?
In such cases, to reduce the overall effort for commissioning the system, we will evaluate the criticality of the requirement in a manner similar to GxP evaluation, and if the function is critical for a specific business process, we will manage it as if it were a GxP critical function.
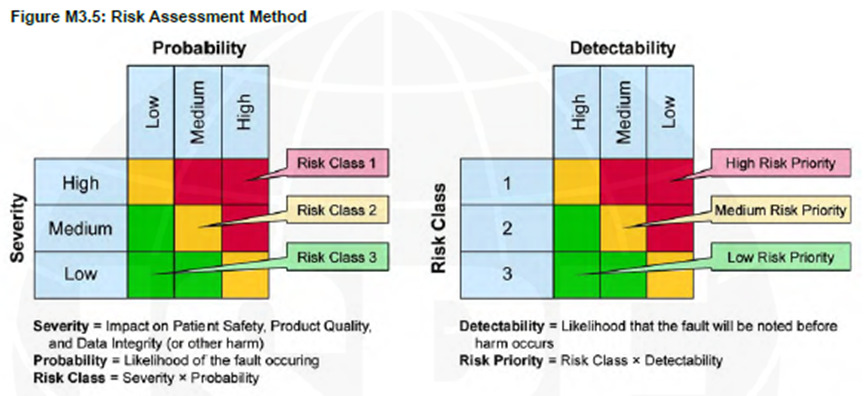
Figure 1: GAMP5 A Risk-Based Approach to Compliant GxP Computerized Systems, Appendix M3
According to GAMP5, before evaluating the Risk Class, we must first determine the Severity, which is defined as "Impact on Patient Safety, Product Quality, and Data Integrity." If you're implementing a system in your organization that manages other critical processes (especially ERP systems), you might want to broaden the definition of "Severity" to include additional questions, which will result in a system with reliable performance with the critical parts defined by the business.
If your company relies on systems whose failure could halt critical processes, alter the final product, or incur enormous costs, you should take extra precautions to ensure the system consistently produces the desired results and that there is objective evidence to support this claim.
The risk-based validation paradigm widely used within Pharma and Medical Device environments can be simply adapted for use in other fields.
This article was prepared by:

Vitaly Shlimovich
Engineering & validation project manager
For more information about our Validation services visit:




